Navigating the Risks and Rewards of Cloud Transformation
Posted by HANDD Admin on 21st November 2024
 Cloud SecurityCloud TransformationData ProtectionData Security
Cloud SecurityCloud TransformationData ProtectionData Security
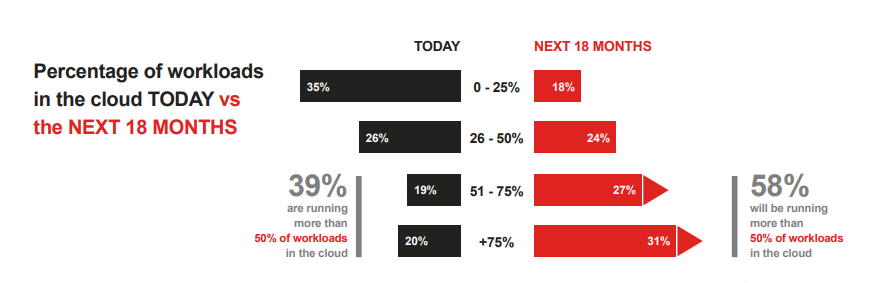
Cloud computing has changed the way businesses work forever. In its infancy, cloud computing offered little more than pay-as-you-go virtualisation, where compute resources were effectively rented from a provider for the duration needed and businesses were billed accordingly. The flexible scalability that the cloud offered meant that soon enough every organisation in the world had a cloud policy governing their position on adopting and implementing cloud services. Accelerated further by the Coronavirus pandemic and the subsequent hybrid working schemes, almost 60%+ of workloads are now conducted in the cloud – which means cloud transformation continues to be a key strategic business focus.
WHAT IS CLOUD TRANSFORMATION?
Cloud transformation is the term applied to a company’s strategic decision to move all or some of its operations, applications, and data from local on-premises servers to cloud-based technology.
This shift is aimed at enhancing the flexibility, scalability, and efficiency of business processes while potentially reducing costs associated with maintaining physical infrastructure. This includes adopting new tools for collaboration, data analytics, and customer relationship management, as well as revising security protocols to ensure data is protected in the cloud. The transformation is not just a technological upgrade but also a cultural shift that encourages innovation, agility and a more data-driven approach to business operations.
Cloud computing has come a long way from simply being a rental service. Today, the term extends to include Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS) delivering different ownership models and flexible costs to consumers for service delivery in a way that meets their business needs. Each of these cloud models comes with benefits but naturally also new risks to the data stored on or consumed by it.
WHY IS CLOUD TRANSFORMATION A DATA THREAT?
Not all cloud applications or environments are sanctioned by your organisation, and not all will have the same level of security and control as your on-premise environments. External cloud environments and technology are not under your control, which means you are reliant on the provider’s commitment to security and safety when handling your precious data.
This alone brings with it some risks; factors to consider in your cloud transformation project:
- Data Security and Privacy Risks
When transitioning to the cloud, sensitive company data is moved from local servers to cloud servers, potentially exposing it to vulnerabilities. The reliance on third-party cloud providers means businesses must trust these providers to maintain robust security measures. This includes protecting data from unauthorised access, breaches, and leaks. - Compliance and Regulatory Challenges
Businesses are often subject to various regulations regarding data handling and privacy, such as the GDPR. Cloud transformation can complicate compliance as data may be stored in multiple locations or jurisdictions and possibly governed by different laws and regulations. - Loss of Control
Using cloud services often means ceding control over certain IT functions and relying on cloud service providers for performance and security. This dependency can be a significant risk if the provider experiences downtime, security failures, or changes in service policies.
WHAT IS HAPPENING NOW, AND HOW DOES IT AFFECT YOUR DATA?
Cloud services extend a lot further than IaaS and aspects of both SaaS & PaaS are prevalent across most organisations. The ability to access information and services regardless of time or locality and the benefits of scalability see cloud transformation as a continued area of business focus.
Cloud services, regardless of their type, do not come without risk and, much like with adopting Artificial Intelligence, IT and Security teams should pause to think about how they’re protecting the information accessed and used within these platforms. With data now held outside of your organisation (basically on someone else’s computer), should a breach to that provider occur, understanding what data types and how much data has been exposed is vital – particularly when overlayed with compliance legislations that place renewed importance on incident reporting and the privacy of individuals and come with hefty fines.
Misconfiguration of new platforms and resources, and oversharing of data, both by administrators and employees, could see sensitive data exposed on new platforms without a clear understanding of the information involved or how to remediate such exposure. The drive to explore new technologies through models such as CI/CD frameworks and DevOps means data is continually added to platforms without a full understanding of the blind spots created by security measures and the resulting increase in risk.
The sheer number of cloud applications with the capacity to consume and collect data within an organisation requires specialist understanding. This can be achieved via a third-party toolset or through configuration of the platform itself. The fact that any service or platform is accessible from everywhere by anyone is both a blessing and a curse. There must be suitable measures in place to prevent misuse of the data and avoid it being unwittingly compromised for example, by downloading it onto personal devices.
As cloud providers make the adoption of cloud compute services simpler and speedier, attackers too can harness these systems to deliver their offences against organisations. Fake websites can be deployed in seconds, distributed phishing campaigns and botnets created at scale within moments and worldwide networks built to execute malicious code previously unattainable without expensive physical hardware.
WHAT FRAMEWORKS, REGULATIONS AND LEGISLATION EXIST?
All existing data protection regulations including the GDPR, PCI-DSS and ISO27001 apply equally to the adoption of cloud technology.
When it comes to policing your data inside of a cloud provider’s network, an organisation should still be able to identify and report what data has been migrated to the cloud and how it is being used or stored within cloud tools. This can be easier said than done as many solutions now reside outside of the corporate environment. When choosing a cloud provider, check for accreditations such as ISO 27001 or that they follow the Cloud Security Alliance (CSA) Security, Trust & Assurance Registry (STAR) programme. The CSA STAR encompasses key principles of transparency, rigorous auditing, and harmonisation of standards, offering cloud service providers a way to demonstrate their security capabilities.
SOC 2 certifications also indicate that the provider is applying appropriate security, availability, confidentiality, integrity and privacy controls.
HOW DO YOU MITIGATE RISK FROM CLOUD TRANSFORMATION?
Take a Strategic Approach: To mitigate risks, businesses must adopt a strategic approach to cloud transformation. They should conduct due diligence on potential cloud providers, ensure robust data security measures, and the existence of a clear compliance strategy to handle regulatory requirements. By addressing these challenges proactively, businesses can leverage the benefits of cloud transformation while minimising its threats.
Define Sanctioned and Unsanctioned Cloud Tools: Provide employees with the right tools to do their jobs. This prevents them from seeking out and adopting unsanctioned cloud tools which are harder to police. Create policies which are not overly restrictive within your cloud platforms, endorse the right level of sharing and feature adoption to prevent the data being unknowingly used in other tools.
Apply Policy Based on Data Classification: Allow sharing of public information but wrap extra security around uploaded sensitive data by understanding what it is and its classification. This can be easier by adopting guidelines such as NIST (National Institute for Standards and Technology).
To secure your cloud computing services, SASE, CASB or any integrated DLP policies in the cloud environment are always the first stop. This can help with the application of stringent data and technology safeguarding rules to prevent insecure configuration of the environment or actions against certain data types. The number of cloud services available is daunting and it will never be possible to block every one of them, especially without the correct tooling.
If you are embarking on a cloud transformation project or need specialist expertise, additional resources or a fresh perspective, we’re here to help. Contact us at hello@handd.co.uk or request a call back to ensure your project meets all requirements and exceeds expectations.
Read our case study ‘Securing data in a modern hybrid environment’.
Learn more in our Guide ‘Data Security and Data Protection in 2024‘, where focus on more common projects, initiatives and areas that we feel need particular attention throughout 2024 and beyond.






















