NIST Cyber Security Framework 2.0 – A New Dawn?
NIST Cyber Security Framework (CSF) has been a set of guidelines and approaches adopted by organisations and vendors across the globe since it’s inception in 2013 through 2014. Born in what many of us would argue simpler times (AI was just what happened in the Will Smith film iRobot) under the Obama administration the National Institute of Standards and Technology (NIST) set about providing a framework to safeguard the cyber security of Critical Infrastructure.
What NIST produced has been used in numerous organisations to bolster their approach to securing networks and operating procedures, used in products by vendors, used by consultants as a measure of cyber maturity and just generally adopted with open arms by the industry as a whole.
To many of us Identify, Protect, Detect, Respond, Recover has become second nature to how we categorize controls, product sets and approaches to what we do for a living.
There have been updates since the birth of CSF, in 2018 we saw v1.1. Since then despite cloud proliferation, working practice changes since the pandemic, MFA, Zero Trust & AI drive change across many other frameworks and legislations, until 2022 NIST remained unchanged.
In February of 2022 the process started to improve the good old CSF a process which ended on 26th February with the official introduction of v2.0:
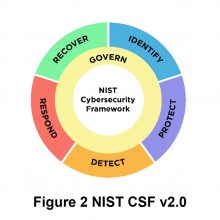
What’s changed then? Firstly, they’ve dropped the Critical Infrastructure label, not a bad shout given the breadth of organisation types using the CSF as a measure of good practice. On top of the five core functions or pillars already available, they’ve overlaid “Govern” to give a consistent approach to risk management regardless of activity and management of each individual initiative area.
Like other legislation we’ve seen in recent months, there is renewed importance around the supply chain and how organisations have become so interlinked and reliant upon ICT, outsourcing and the risk posed therein by that reliance.
NIST have provided a bunch of tools and implementation examples to help foster adoption of v2.0 they can be found here.
What will it mean for those looking to adopt v2.0? More policies expected in a nutshell, again like the other legislation HANDD have studied in the early part of the year, what’s your organisations Risk management strategy, expectations, measurement of and decision-making process will all fall in and around the new Govern function.
If you’re adopting the new update and need support in analysing where you may fall short or what introduction of governance could mean in your business, then HANDDs team of Cyber Security experts are as ever happy to assist and advise on the best path forward to adopting v2.0. Get in touch with us at info@handd.co.uk or call us on +44 (0)8456 434 063.
























